It's a standard alarm signal protocol that enables alarm panels to communicate alarms and other incidents with monitoring firms.
How does the surgard protocol work?
The surgard protocol uses a contact id format to send information about an alarm or incident. This information is then used by the monitoring company to find the reason or exact location of an alarm.The surgard protocol uses a unique identifier for each object. This identifier is used to track location of the object.It also contains an Event ID, which may be used to determine what occurred and Zone ID and Sector ID to identify the exact location of the object.
Sucrgard Contact Id Message Format
ACCT MT QXYZ GG CCCExample:
234 18 1131 01 015where:
ACCT = 4 Digit Account number (0-9, B-F)
MT = Message Type. This 2-digit sequence is used to identify the Contact ID message to the receiver. It may be transmitted as either 18 (preferred) or 98 (optional).
Only receivers with a 18 or 92 are compatible with the American and Canadian standards. The new receiver will work in both countries, so you may use either the 18.
Q = The Status report contains the following information: 1 = New Event or Opening 3 = New Restoration or Closing 6 = Previously reported condition still present (Status report).
XYZ = Event code (3 Hex digits 0-9,B-F).
GG = Group or Partition number (2 Hex digits 0-9, B-F). Use 00 to indicate that no specific group or partition information applies.
CCC = Zone number (Event reports) or User # (Open / Close reports ) (3 Hex digits 0-9,B-F ).
How to integrate device with the Surgard / Contact ID Protocol connected via COM por or TCP/IP
Alarm front is central station software that supports Surgard Contacit ID.Testing and configuring the COM port
Let’s assume you have an alarm receiver which isable to transmit data into internal systems via Surgardprotocol connected to your server via COM port.
First, you need to check that device is connected and configured correctly. To do that:
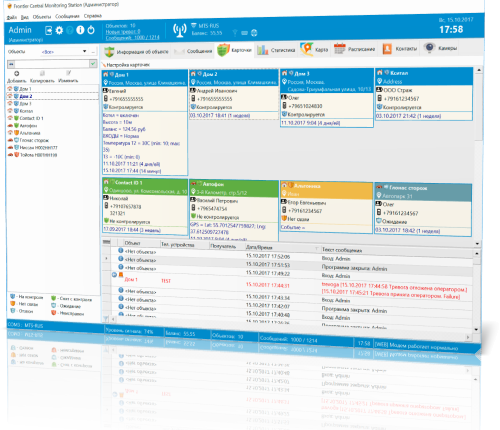
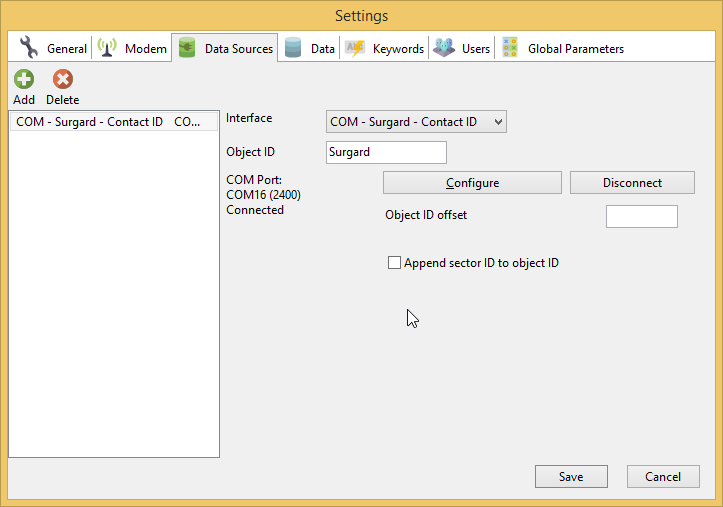
1. Add the COM - ASCII devide on the Data Srouces tab of program’s settings. We use the COM-ASCII protocol interfaceinstead of Surgard to check that device and COM port are configured correctly and you are able to receive data. After will will switch to Surgard protocol.
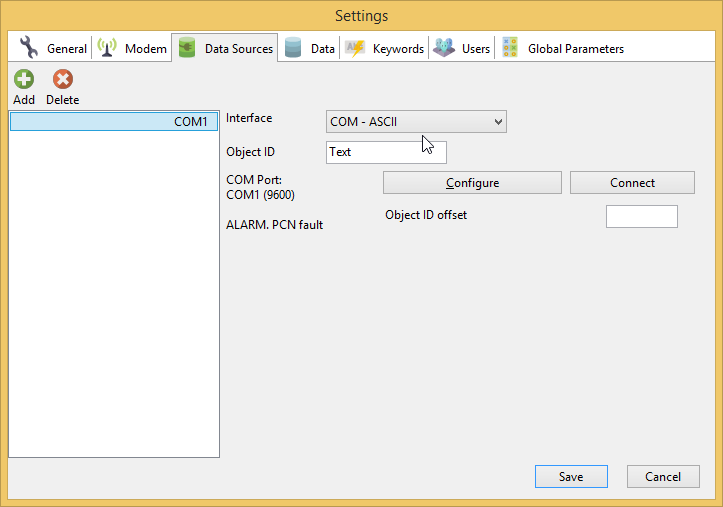
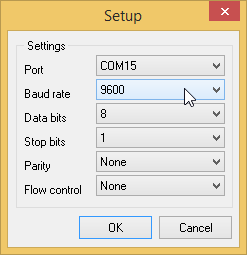
Specify the COM port that is used to connect your alarm receiver the Baud rate if required. The most popular baud rates are 9600 and 115200. If you are not sure
which one is used by your alarm receiver, try both of them. Button to connect to your alarm receiver using the configured COM port.
Click the Save button to exit from options with saving.
Generate an alarm for your alarm receiver.
Go to the Settings tab of the main window. If your COM port settings are valid and device connected and configured correctly, you will see a message in
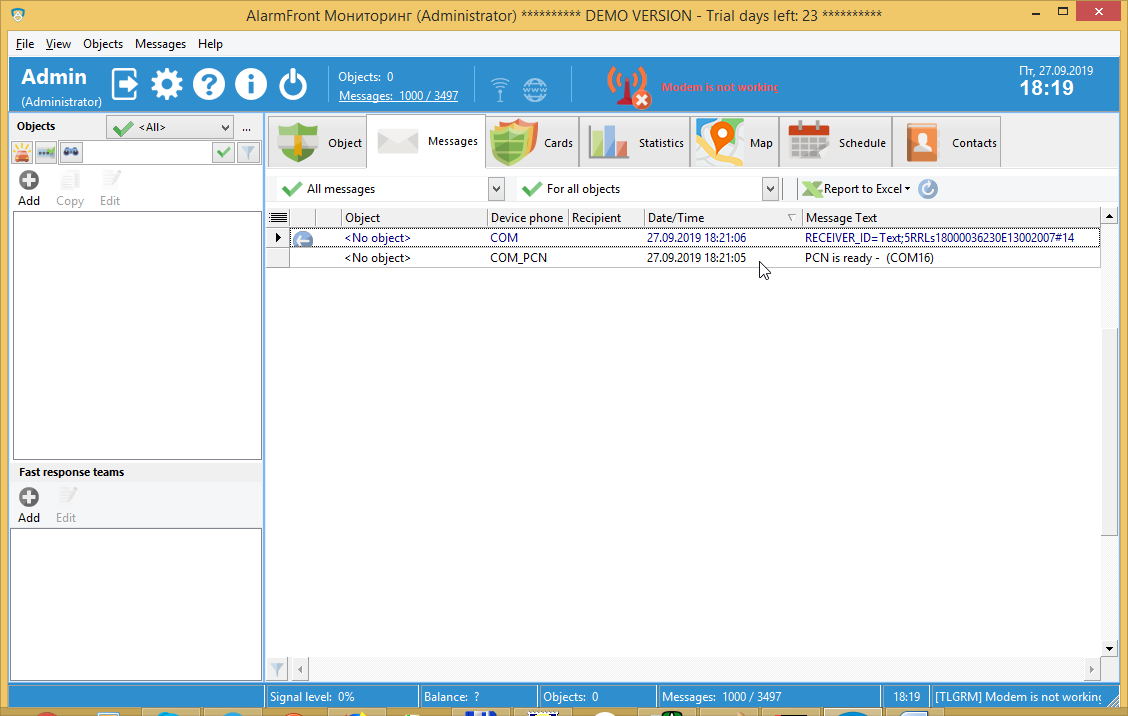
The message in Surgard protocol should like If you do not receive such message, check thatthe alarm receiver is plugged to specified COM port and that it uses the same baud rate that you entered in the COM port settings. Also check that alarmreceiver is configured to send notifications via Surgard.
Generate alarm message once again.
On the Messages tab now you will see the data retrieved from this message.
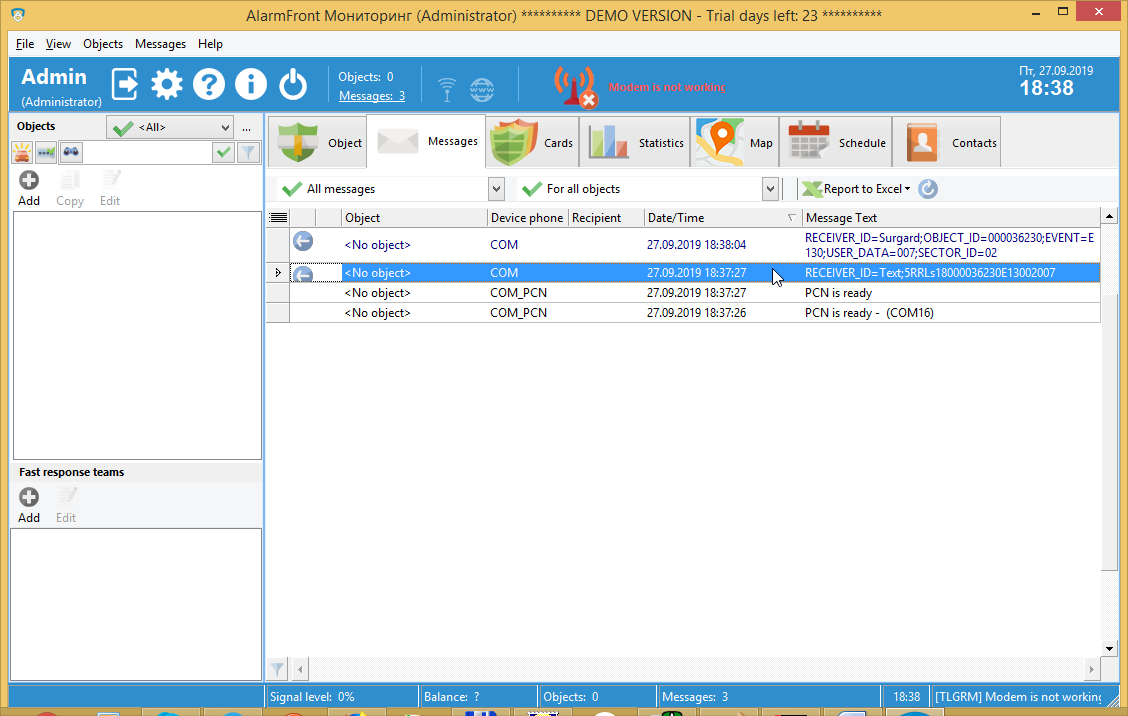
Now message looks like: RECEIVER_ID=Surgard.
It contains OBJECT ID, Alarm code, Zone and Partition ID.
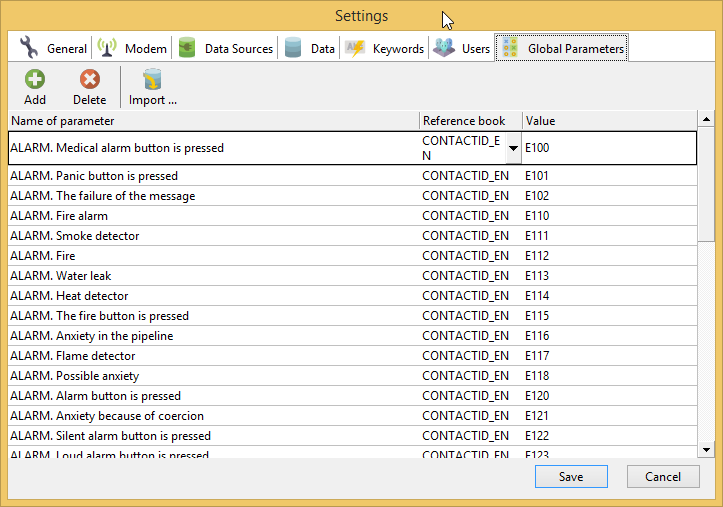
To have interpretations of Contact ID alarm codes, go to the Global Parameters tab of program’s Settings and import the ContactID_en.csv file from program’s folder.
Creating an object
Now we are ready to create a first object.Only alarm messages that assigned to objects are displayed as Alarms tooperator. Messaged is assigned to object by value of the OBJECD_ID field. We will create an object and specify value of its
parameter ID to given OBJECDT_ID.
They are several ways to create an object
First, you may create an object manually using an Add button on Objectspane. You may use Surgard Contact ID template for it.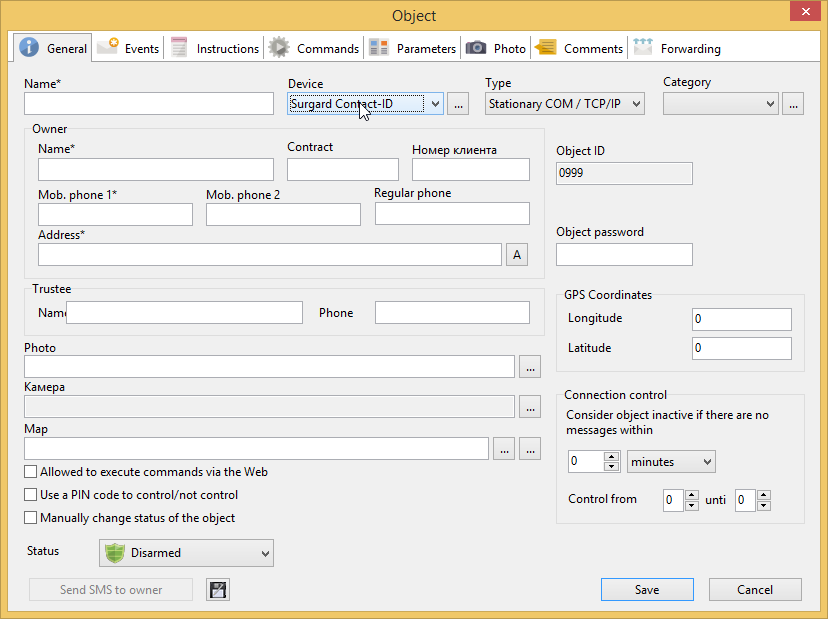
After you fill in all required field of an object card. Go to the Parameters tab
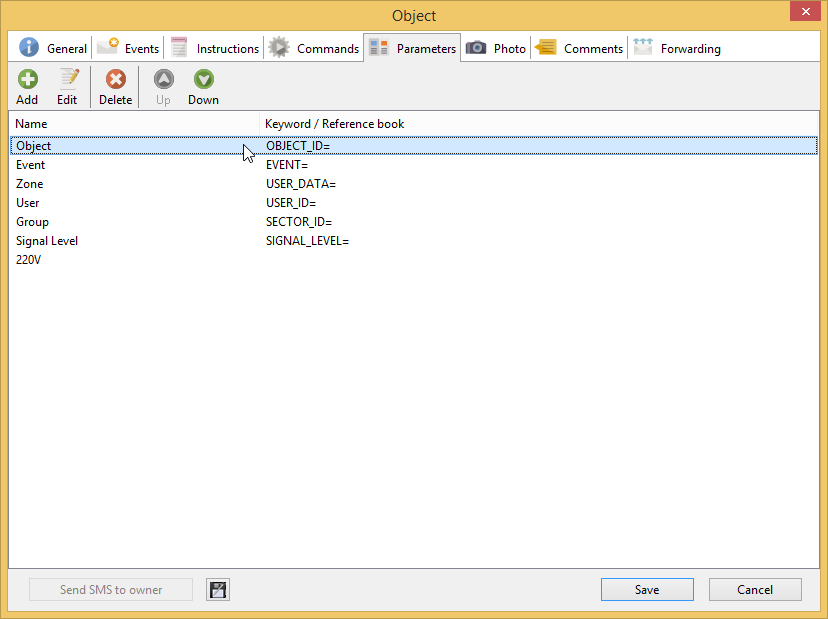
Enter the value you got from the message in the OBJECT_ID
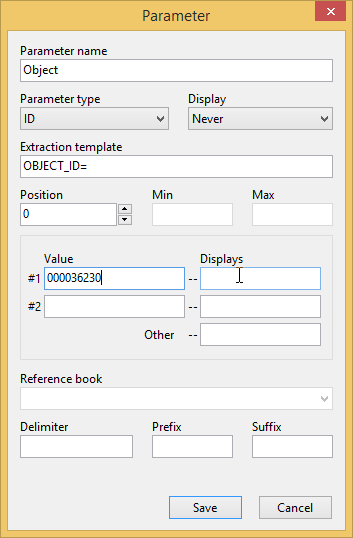
Program can create an object for you automatically. Right click on the message and select the Create object form message menu item.
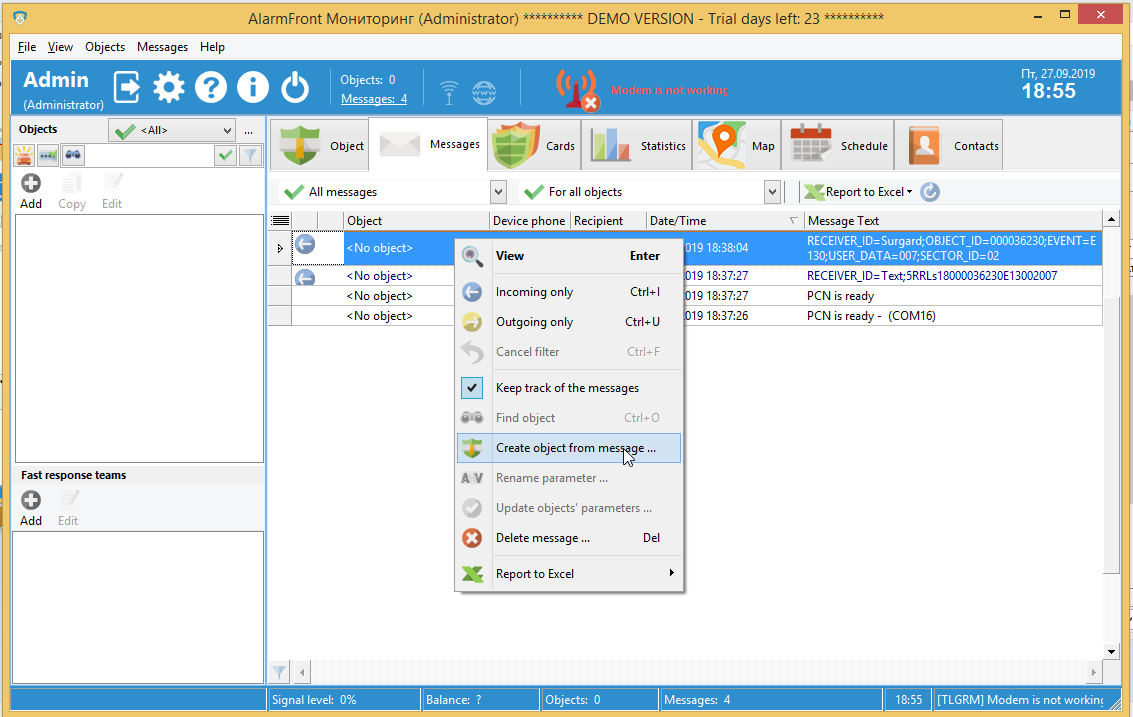
We have an object created now. All message with OBJECT_ID=000036230 will be dispatched to it.
The next message will cause an alarm displayed.
Generate an alarm message to test it.
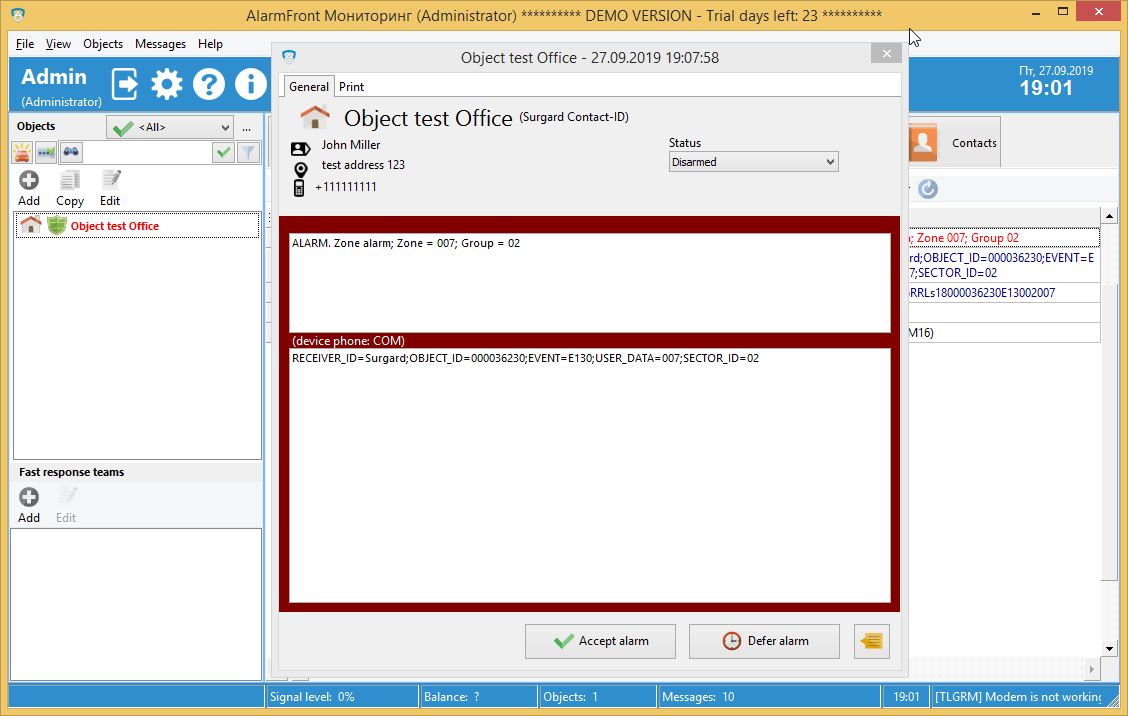
Now you see an alarm message with an Alarm message (Zone alarm), Partition (02), Zone = 007.
Now you may add names to Zone and Partition codes in the Events tab of object’s properties.
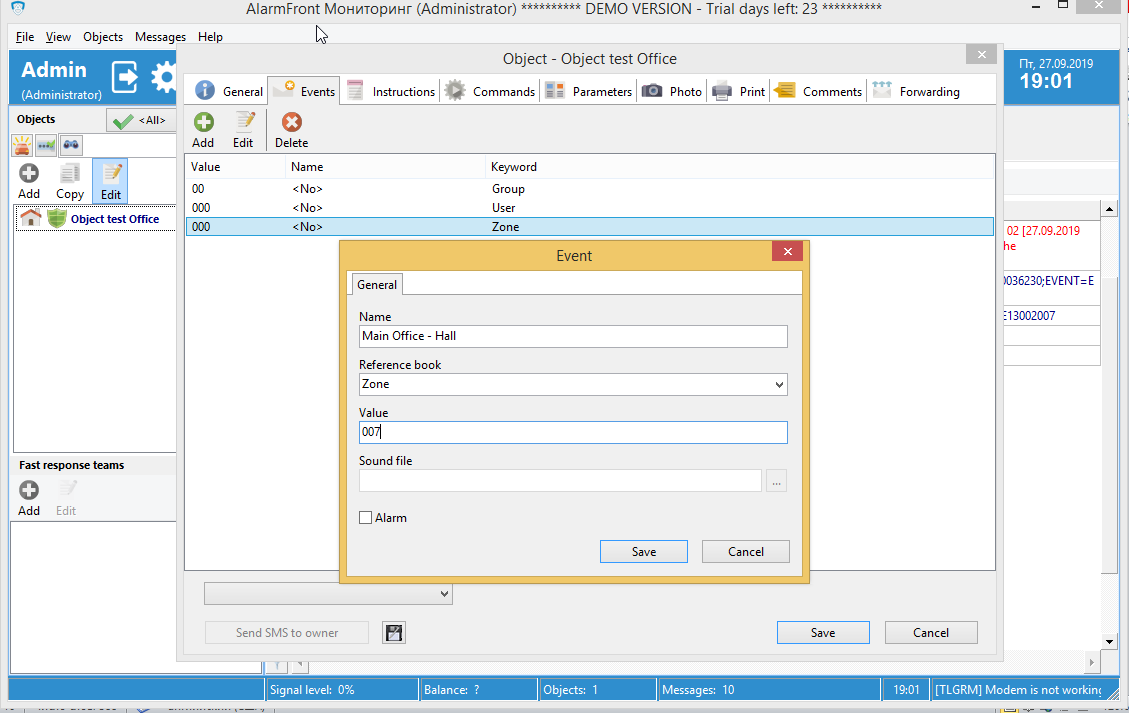
Next message will contain Zone name instead of Zone number.
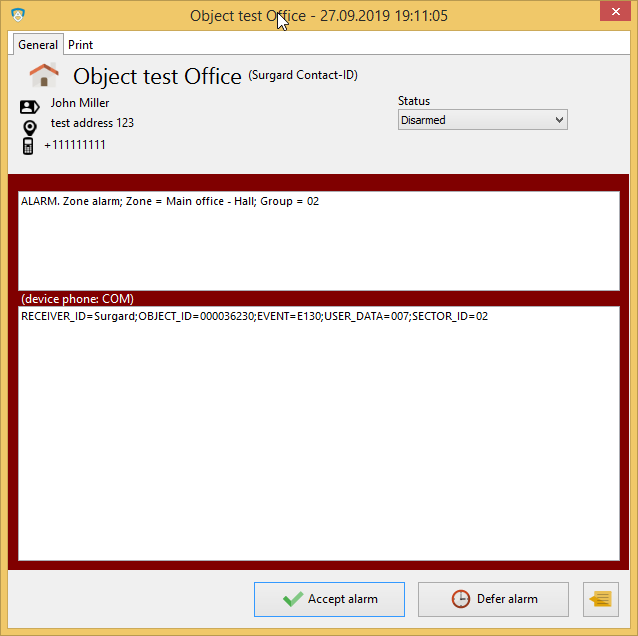
You can do the same for Partition codes to name Partitions (also names as Group).
Dealing with partitions as separate objects
Some alarm companies have several clients on one object. Each client as assigned to one of object’s partitions (may be also named groups or sectors). Program is able to work with partitions like with separate objects. To enable this feature, go to Data Sources tab and enable the Append sector ID to object ID checkbox.This will cause that next time when you receive an alarm message, it will have an OBJECT_ID field with appended sector ID.
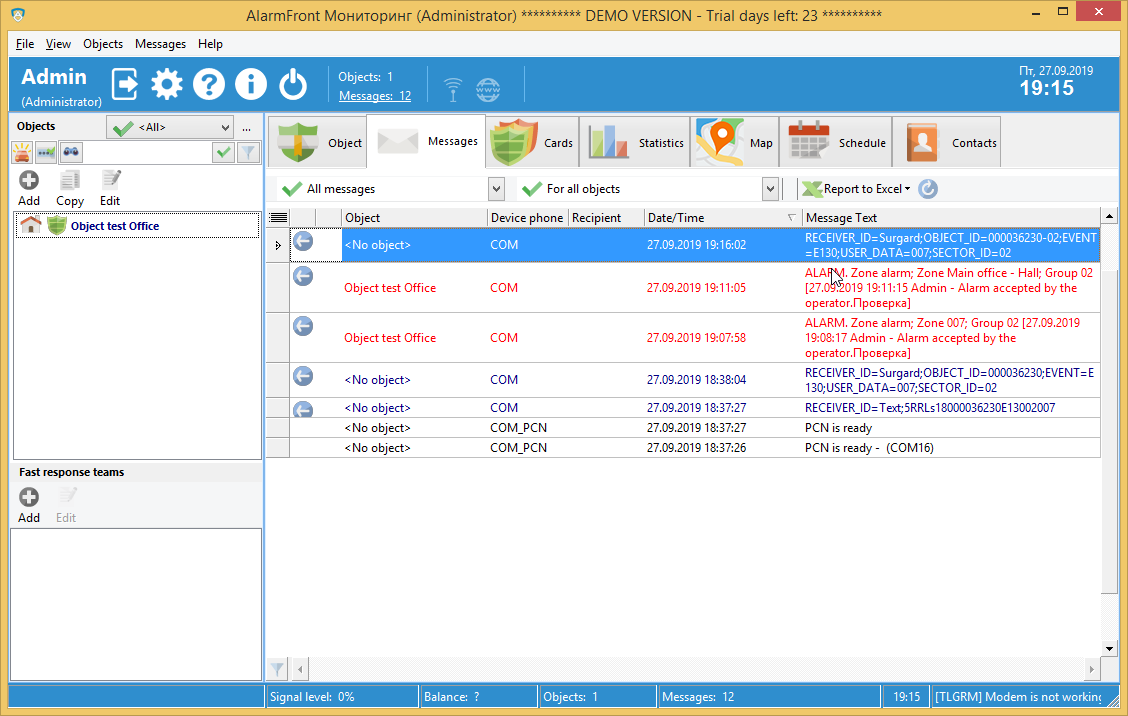
The message will look like this
RECEIVER_ID=Surgard_ID=000036230-02;EVENT=E130;USER_DATA=007;SECTOR_ID=02
It has sector id=02 appended.
Now you will need to edit object’s parameter Object ID and set its value to 000036230-02.
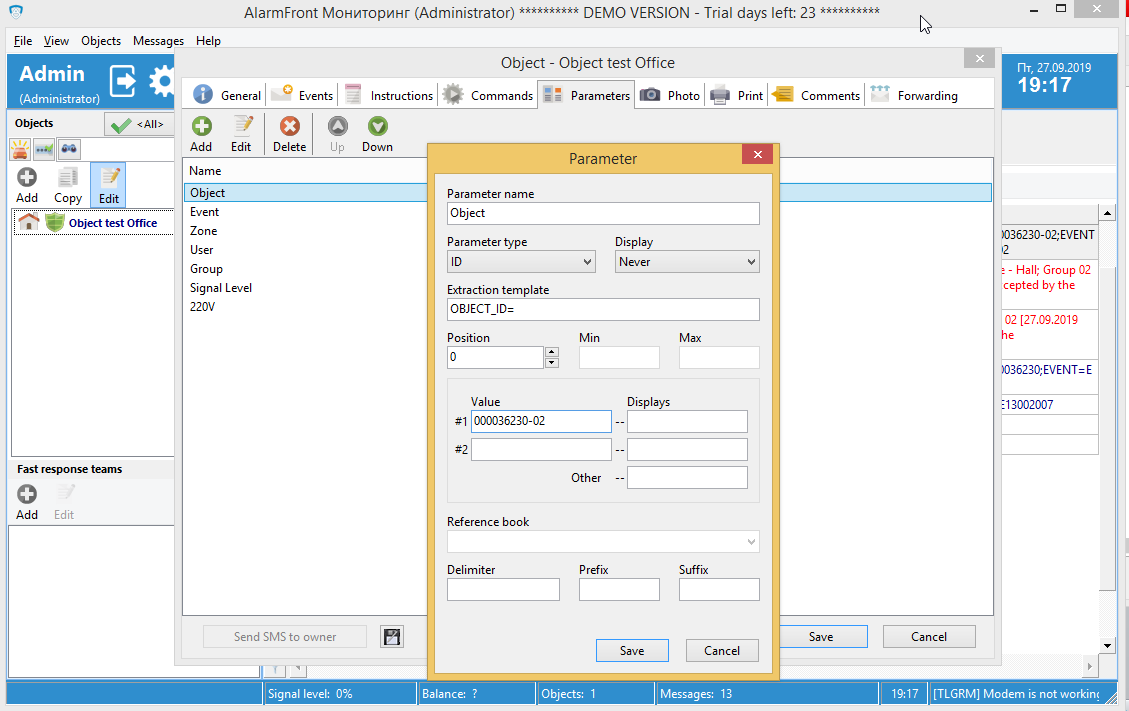
Now object will receive only messages that come to Partition 02.
However, if you have some objects that assigned only to ONE client with multiple partitions, this is also ok.
System will looks for objects with ID= 000036230-02first and if it do not find it, it will look for object000036230 and if it exists, will assign message for it.
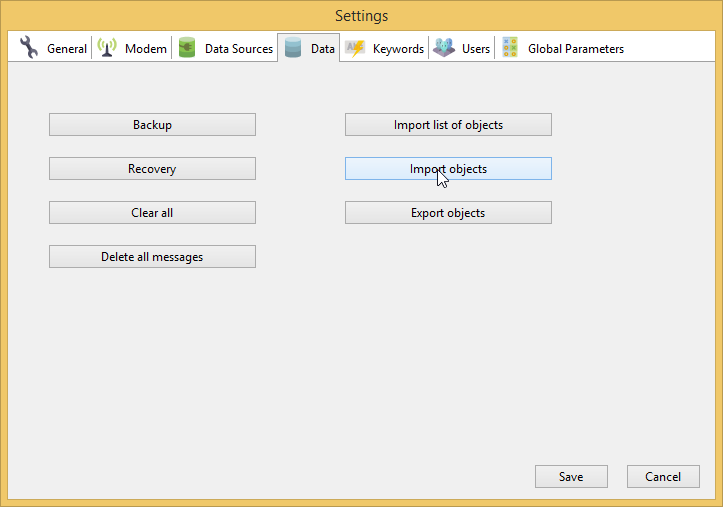
Importing object from CSV file
If you need to create big list of objects, you may use CSV file import.Prepare the CSV file with the following columnsphone;Primary device phone;Secondary.
device phone;Category;Contract;Template.
Import it in the program’s settings on the Data Tab using Import objects button.
Why is the surgard protocol important?
The surgard protocol is important because it allows alarm panels to communicate with monitoring firms. This communication is essential for the proper functioning of an alarm system. Without this protocol, alarm systems would be much less effective.What are the benefits of using surgard protocol?
- It's simple to put in place.
- To send alarm notifications, you don't need a lot of traffic on the network.
- Can be used over phone line
Disadvantages about Surgard protocol:
- Do not have CRC to validate sent data
- Surgard, unlike other protocols like SIA DC09, isn't very flexible.
- There is no event date and time in the message